June 6, 2017
The massive global cyber-attack on May 12 demonstrated a large lesson regarding disciplined patch management. The aggressive, insidious WannaCry ransomware impacted over 400,000 systems in more than 150 countries running Windows-based operating systems (OS). Ironically, were it not for an accidental hero registering a domain, it could have been much worse.
Consequently, the attack was a wake-up call, most notably for businesses running older systems and business with deficiencies in their software patching practices.
Hacking is a Weapon, not a Game
Hacking isn’t a game played by computer geeks as a challenge anymore; it is nothing less than a potential weapon of mass destruction. Bad actors are everywhere in the cyber world. Manned and unmanned robots roam the vast spaces of the internet 24/7 knocking on unlocked doors seeking to enter and create havoc, destruction and theft. Hackers are ready to exploit known software vulnerabilities that result from poor software patch management programs.
Fair Warning
According to The Washington Post, the NSA warned Microsoft about a leaked exploit. In addition, US-CERT issued an urgent security advisory in January and urged businesses to disable support for the protocol. Finally, Microsoft released patches to fix the vulnerability that allowed the worm to spread across networks.
Nevertheless, many businesses didn’t take action. By and large, infected computers in the attack were considered out-of-date devices that for some reason were deemed not worth the price of upgrading. In some cases, computers involved in manufacturing or hospital functions were left unpatched because of potential disruption to critical operations. Not surprisingly, hospitals were among the hardest hit.
Unfortunately, anyone directly responsible for their software hygiene can’t avoid the facts. Today, there are millions of older Windows systems running, and still running strong, and bad actors know that.
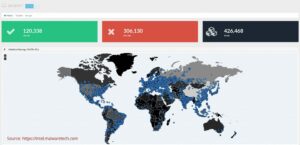
Scary stats: 19 days after the WannaCry ransomware attack started, over 72% percent of affected systems remained offline.
A Wake-Up Call For Disciplined Patch Management
In most cases, IT likely knew about the update but did not take immediate action. This attack is a wake-up call to assess your patch management strategies.
With the recent ransomware attack, as well as another patch to a critical code-execution vulnerability for Linux and Unix, regulated industries are scrambling to come up with a plan. Without a disciplined patch management program, data compromise will come with a heavy cost, where service and device interruption can, at worst, put lives in danger.
Patch Management Regulation in the Energy Industry
One industry where a disciplined patch management approach is required to stave off exploitation of cyber vulnerabilities is the energy and utilities industry. The industry understands the immense threat of cyber attack to the Bulk Electric System (BES). This type of exploitation has the potential to damage the power grid and to leave people without power, in the dark and cold, for days or even months.
As a result, the North American Electric Reliability Corporation (NERC) has put into place mandatory regulations for cyber security systems management, including software patch management (Standard CIP-007). Energy and utilities providers risk large financial penalties for non-compliance.
Take a Page from NERC
AssurX works closely with energy companies who are implementing cyber asset compliance. It is undoubtedly the most strategic approach to cyber security we’ve seen. Other industries should look at NERC CIP regulations as a model to be followed in developing disciplined practices, policies and procedures for asset patch management.
By assets, NERC doesn’t just mean laptops and desktops. Any device within the security perimeter is regarded as a potential vulnerability.
Conclusion
The WannaCry attack raised pressing questions about software patching and vulnerability disclosure practices. There isn’t any doubt an attack of this magnitude can happen anywhere, any time to any system software or firmware.
A proactive approach to defending your enterprise cyber assets is not an option anymore. Start strategically assessing your discipline for tracking your assets and applying patches. AssurX works with major utilities implementing processes with our compliance management system for cyber asset inventory and patching. The AssurX platform creates a disciplined regimen for patch management.
Contact AssurX to learn more about a compliance management solution to protect your cyber assets.




